Active Directory Part 1: PowerShell
We will start this series to talk about one of the most known built in tools in Microsoft, PowerShell. We will discuss its multitude of functions and its connection to many exploits within Active Directory.
Active Directory (AD) serves as the cornerstone of modern enterprise networks, enabling centralized user management, authentication, and resource access control. However, the complexity and criticality of Active Directory also make it an attractive target for attackers. To safeguard your organization's infrastructure, it's crucial to be aware of the common pitfalls and vulnerabilities that can undermine Active Directory security and adopt effective mitigation strategies.
In this blog series, we will embark on a journey through the intricate landscape of Active Directory, shedding light on the most prevalent pitfalls and vulnerabilities that organizations face. We will explore the potential consequences of these weaknesses and provide practical mitigation techniques to fortify your Active Directory environment against potential attacks.
PowerShell
PowerShell has emerged as a game-changing tool, revolutionizing the management and automation of Active Directory tasks, as well as of Windows environments as a whole. With its robust scripting capabilities and direct integration with Active Directory, PowerShell empowers administrators to streamline tasks and improve efficiency.
PowerShell lives up to its name, it is very powerful. With PowerShell an adversary can do most of the reconnaissance phase in the Cyber Kill Chain on both local and remote computers (assuming that the remote machine has PowerShell remoting enabled). While there are other tools for performing reconnaissance, such as nmap and Metasploit, PowerShell can be utilized in a stealthier manner as it’s a tool that comes by default with most Windows computers. The stealthiness comes from the fact that Administrators tend to whitelist PowerShell and ignore alerts associated with it. Using tools that are already present on a machine is often referred to as LOLBins (Living Off The Land Binaries) which can be used together with PowerShell.
The thing with PowerShell is that it is not an offensive security tool from the beginning, it was not intended to be at least. It is therefore important to restrict its usage, for example: does Alice from sales need PowerShell, or the capability to query Active Directory for a PowerShell session?
AMSI and PowerShell
AMSI stands for "Antimalware Scan Interface," and it's a feature in Microsoft Windows designed to help protect against malware and other threats. AMSI enables real-time scanning and detection of malware by scanning data in its located processes. The data which is scanned gets a score if its malicious or not, this score is calculated based on various signatures and parameters. Because it’s based on a value, it can sometimes block things that are seamlessly harmless, in the photo below you can see that we try to run the string “amsiutils”, and that gets blocked by AMSI.
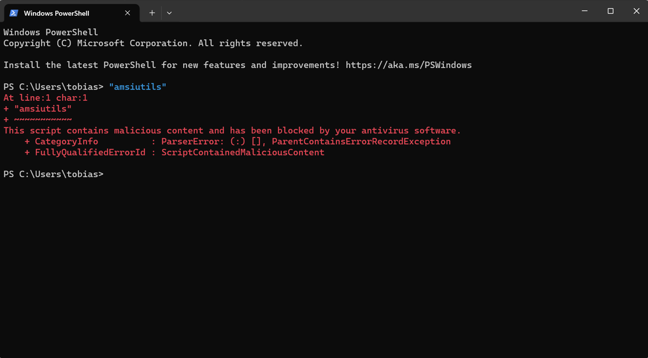
AMSI was created after PowerShell which means that earlier versions of PowerShell do not have the security features that AMSI provides. A common attack path for adversaries is to perform a “Downgrade attack” which effectively makes the process running PowerShell an exemption from the Antivirus solution.
Ever since AMSI was brought into the picture, multiple bypass methods have been developed. A deep dive of AMSI blogpost will come where we investigate the bits and bytes on how it works.
Day to day usage
IT administrators commonly use PowerShell to automate various tasks, manage systems, and streamline administrative processes. Typical use cases include user account management, where they can create user accounts, reset passwords, and disable or enable user accounts. Group policy management is another area where administrators use PowerShell to manage group memberships and audit group memberships. Any administrator that has managed GPO knows that doing it manually is tedious.
In terms of server and system management, PowerShell can be employed for tasks such as system monitoring and event log collection. Network configuration is streamlined with PowerShell, allowing administrators to manage network settings and perform network diagnostics. PowerShell can also automate software deployment and updates using scripts, which can install or uninstall software and manage Windows updates. In environments that have Windows 11 systems, we see that more companies are leveraging the new built-in package manager “winget” for installing and managing software, but the overall majority still has exceptions for PowerShell.
PowerShell can handle file and folder management tasks which include operations like copying, moving, and deleting. Additionally, administrators use PowerShell to manage file and folder permissions. Active Directory management is made more efficient with PowerShell, allowing admins to query and update attributes for users and other objects.
Reporting and logging activities are also facilitated by PowerShell scripts, which can generate reports on various aspects of the IT infrastructure and log activities for auditing purposes. Automation of repetitive tasks is a key strength of PowerShell, allowing administrators to schedule tasks and perform bulk operations.
Moreover, PowerShell is not limited to on-premises environments; it extends to cloud management as well. IT admins can use PowerShell to automate tasks in cloud environments, including Azure and AWS.
PowerShell's scripting capabilities and integration with various Microsoft and third-party technologies make it a valuable tool for not only IT professionals, but as well for people who want to cause you harm.
Enumeration
Enumeration is a step in the reconnaissance phase in the Cyber Kill Chain. PowerShell can help gather information about the Active Directory. There are several things that may be interesting to enumerate in Active Directory such as users, groups, devices, policies, domain trusts etc. The aim of the reconnaissance phase is for an adversary to gather as much information as possible about the target to find a vulnerability that can be exploited to get one step closer to the objectives of the attack.
PowerView
To uncover potential vulnerabilities, identify misconfigurations, and assess the overall security posture of an AD environment, security professionals turn to powerful tools like PowerView. Developed by Will Schroeder (@harmj0y) as part of the PowerSploit project, PowerView is a game-changing tool for Active Directory reconnaissance and exploitation.
PowerView is an offensive module that can be loaded to PowerShell that contains multiple scripts that makes it easier to navigate in the AD environment. This module has a plethora of capabilities.
Enumeration with PowerView
PowerView can provide several cmdlets (PowerShell commands) that help gather information about the Active Directory.
Here are some common ways to enumerate different components:
- Enumerates a domain’s users.
>Get-DomainUser -Domain windomain.local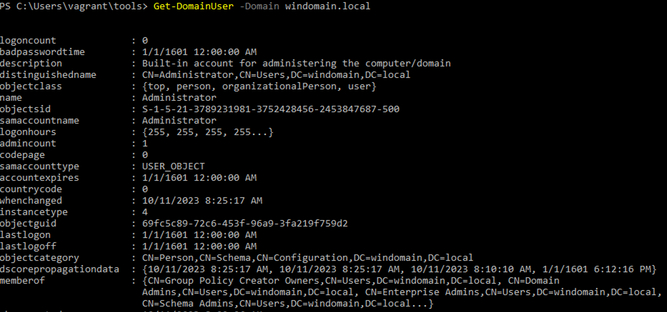
- Enumerates users within the domain group” Help Desk Level 1”.
>Get-DomainGroup -Identity "Domain Guests"
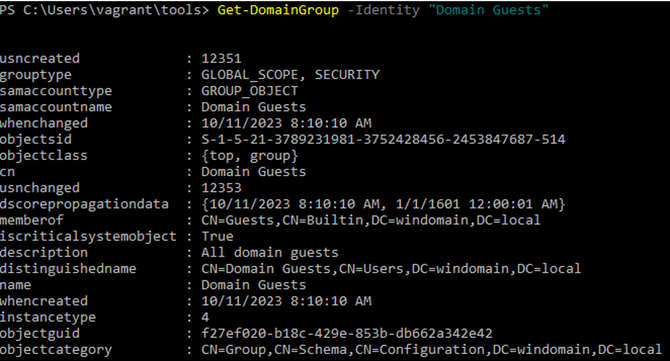
It is worth noting that you do not need PowerView to for example enumerate users, it can be run using Active Directory module as well:
>Get-ADUser -Filter *

C# Scripting
It is also possible to run C# code using PowerShell. This is since PowerShell is based on .NET and by extension can access all .NET libraries. Even though this expands the amazing capabilities of PowerShell, this also introduces security risks. By executing arbitrary C# code in PowerShell, it may introduce security risks if the code comes from an untrusted source. It could also enable an attacker that has gained access to the system to run C# code to execute malicious actions using common C# libraries to obfuscate themselves. Since this functionality is intended it can be harder to detect suspicious activity.
To mitigate these risks, it's essential to follow best practices for PowerShell scripting, including validating and sanitizing inputs, using signed scripts, and limiting the use of external code, especially from untrusted sources. Always exercise caution when executing code obtained from external or untrusted sources.
Other recommendations are:
- Code Review and Analysis
- Behavior Analysis
- Monitoring and Logging
- Whitelisting
- Security Training
- Security Policies
Next
Continuing the journey into the spider web of Active Directory, the next post is about something that we have touched upon already in this post, Domain Trust, and Access Control.
This post is the second in a blog series on Active Directory. You will find the rest of them here (as they are published):
1. Active Directory: Introduction

